Reckon Blog
News and insights for small businesses
Creating customer profiles and personas for your small business
Looking to take your marketing and sales strategy to the next level? Learn how to use customer personas and profiles for your small business.
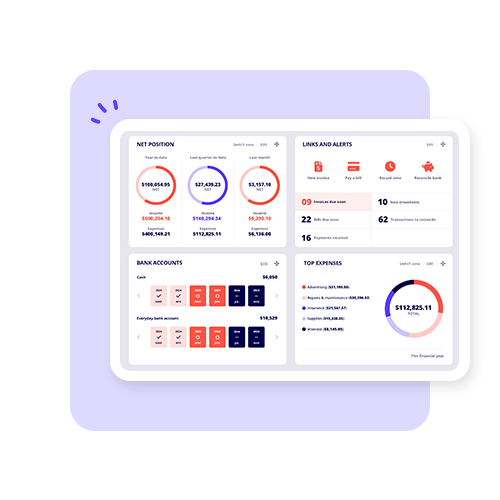
The big changes in 2025-2026 Financial Year: What businesses need to know
The 2025-2026 financial year is full of compliance, tax and employee changes that small businesses need. Read here to get informed.
How to run your business into the ground!
Tired of success? Check out our hot tips on what not to do when running your business.
Follow our social media